It would be great to supply some real-life examples such as an organizations files being encrypted and the attacker requesting payment to unencrypt or a phishing attack coming from a known person asking you to wire money. Kernel mode also known as supervisor mode is where the kernel lives allowing low-level access to memory CPU disk etc.
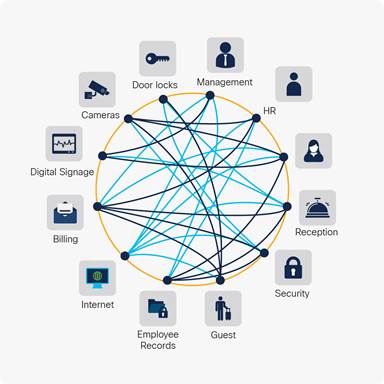
Solutions Intent Based Networking S Next Evolution Policy Integrations Between Multiple Domains Cisco
Regular firewalls block malicious traffic from getting into your systems while a human firewall helps to secure your network.

. To provide a Common Body of Knowledge CBK and define terms for information security professionals the International Information Systems Security Certification Consortium ISC2 created the following 10 security domains for the CISSP credential 1. Select 4 Phishing emails. With the advent of the digital era and an increase in digitisation the amount of data available has increased massively.
Consider RANDOMIZED-QUICKSORT operating on a sequence of n distinct input numbers. March 4 2020 613 pm. The term human firewall refers to a group of people in your business who offer an added line of defense against cyber attacks.
Make adoption easier by strengthening a few weaknesses at a time. We know what a normal firewall is it acts as the first line of defence to block outside threats and create a barrier between secured and controlled networks. In essence it is an environment of mutual trust where employees work towards the.
A human firewall is extremely important to the companys security and overall well-being. Confidential Secret and Top Secret are three security domains used by the US. Which of these things is part of the CYBER domain.
A group of people in an organisation that works towards detecting cyber attacks such as ransomware or phishing attacks that may bypass your computer security system are known as a human firewall. A Human Firewall follows a similar concept using humans your workforce as the barrier between cyber criminals and your infrastructure. When developed fully it works like a regular firewall where it blocks outside threats and creates a barrier between secured and controlled networks.
If you empower your team on cybersecurity you will bolster your other firewalls. We recently discussed the tried-and-true CIA information security triad. It focuses on the understanding and.
Date Time. Dont overwhelm people with too much information at once. Telecommunications and Network Security.
What are the three security domains human firewall. The Security Domains Triad. A human firewall is a structured and ongoing education for the staff on the cybersecurity threat environment.
Write a method called sumArray that accepts an array of floating point values and returns the sum of the values stored in the array. Prove that for any constant k 0 all but O 1nk. Department of Defense DoD for example.
What are the three security domains. With respect to kernels two domains are user mode and kernel mode. Confidentiality keeping secrets secret Integrity ensuring information is not modified and Availability keeping electronic doors open and IT shops humming.
The InfoSec Institute identifies 7 elements required for a successful human firewall approach. Feb 11 2021.

How To Be An Excellent Human Firewall
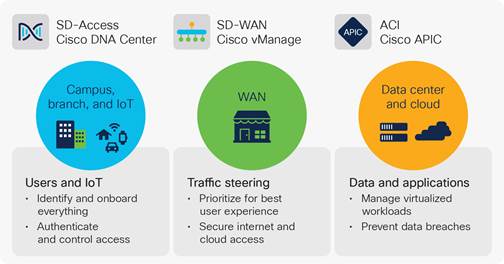
Solutions Intent Based Networking S Next Evolution Policy Integrations Between Multiple Domains Cisco
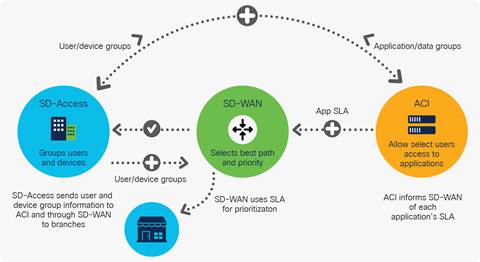
Solutions Intent Based Networking S Next Evolution Policy Integrations Between Multiple Domains Cisco

What Are The Different Types Of Penetration Testing Purplesec

How To Be An Excellent Human Firewall
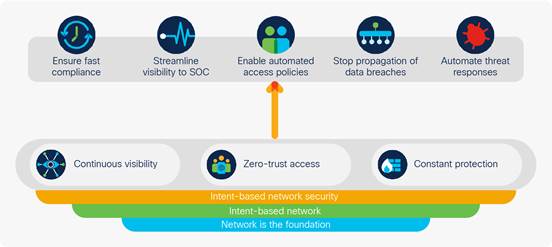
Solutions Intent Based Networking S Next Evolution Policy Integrations Between Multiple Domains Cisco

0 comments
Post a Comment